EXECUTIVE SUMMARY:
This article provides in detail the elements of an Enterprise Architecture (EA) framework that would be selected and deployed at a fictional United States (US) Federal Government contractor called FedCon. FedCon is divided into 3 Business Units (BUs) that are focused on providing Management Consulting, Information Technology (IT) Consulting and Systems Integration (SI) Services in Healthcare, Environment, and Finance.
This article analyzes FedCon in terms of Strategies, Politics, Innovation, Culture and Execution (SPICE) as shown below:
| Stakeholders | Domains | |
| Strategies | CEO, COO, and CIO | Business-IT alignment |
| Politics | BU SVPs, PMO and program/project managers | Technology products and services |
| Innovation | Employees directly interfacing with customers | Technology products and services |
| Culture | PMO, HR and Accounting/Finance | Leverage the massive intellectual property |
| Execution | All employees | Organizational performance |
Based on the above, it is determined that The Open Group Architecture Framework (TOGAF) would be the appropriate EA framework at FedCon since (1) it is supported by multiple vendor tools (2) it is constantly being improved upon and (3) it has an Architecture Development Methodology (ADM) which can be used as a guide.
ABOUT FEDCON:
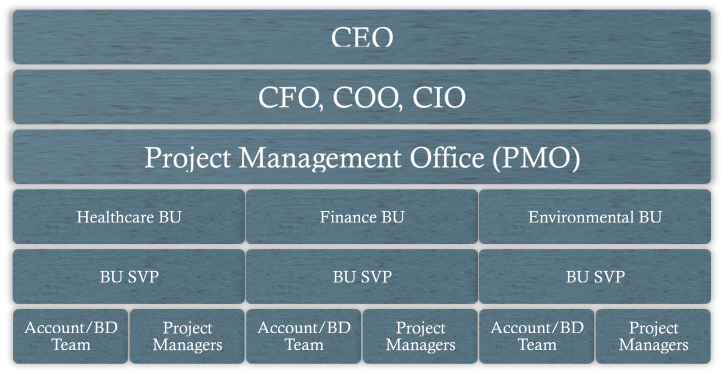
FedCon is a fictional 30-year-old large publically traded US Federal Government contractor that provides Management Consulting, IT Consulting, and SI services to civilian agencies. It has over 5,000 employees nationwide and it is structured into three Business Units (BUs). Each BU has domain expertise in Healthcare, Finance or Environmental information systems. This structure allows the BUs to work directly with the civilian agencies based on their missions. Each BU has its own account/business development (BD) team that reports to the BU Senior Vice President (SVP). The Program/Project Managers report to the BU SVP and provide status updates on programs/projects to the corporate Program Management Office (PMO). The PMO conducts weekly meetings to provide guidance on corporate standards, compliance, and general project templates.
PROBLEM STATEMENT:
Over the past couple of years, FedCon has lost 20% of its business. The CEO has been under pressure by the shareholders to turn the company around. Thus, the CEO hired a management consulting firm to determine what were the pain points within FedCon that were preventing it from staying competitive in the marketplace. The management consulting firm’s report revealed that due to inefficient business processes and outdated technologies FedCon’s BUs were not able to collaborate efficiently to manage business and technology changes. Based on these findings in the report, the CEO mandated the Chief Operation Officer (COO) and Chief Information Officer (CIO) to work together to find areas that they can improve in the next 12 months.
ANALYSIS:
In order to address the CEO’s concerns, the COO and CIO came to the conclusion that in order to help FedCon create a disciplined approach to managing strategic intent and its execution they had to look into the field of Enterprise Architecture. Thus, the COO and CIO decided to standup an Enterprise Architecture Program Management Office (EAPMO) that would report directly to the CIO. Initially, the EAPMO is tasked with determining the high-level criterions to select a framework. This task includes providing elements of the framework to be used and how the framework would be applied within FedCon..
In this article, we assess the feasibility of an EA framework that can be used in FedCon by making observations about Strategies, Politics, Innovation, Culture and Execution (SPICE) factors. These factors would focus on understanding the people, processes, and technologies at FedCon to create an effective EAPMO.
Strategies at FedCon:
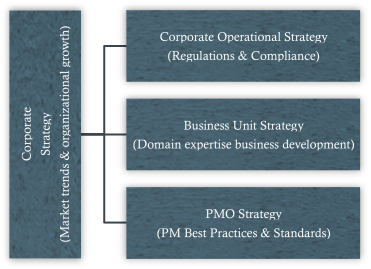
At FedCon, there are multiple levels of strategies that are developed. These strategies include: (1) the corporate strategy determined by the CEO, (2) the operational strategy determined by the CFO, COO, and CIO, (3) the BU strategy determined by the BU SVPs and (4) the PMO strategy determined by the PMO office. This is shown below.
As we can see from the above figure, each strategy layer addresses different domains for the various stakeholders. Even though these strategies are developed to increase the bottom line and decrease costs, they are created in isolation. Additionally, since each BU is somewhat autonomous it can create technology products and solutions for the civilian agencies that overlap with corporate products and solutions. This is a problem since not leveraging the corporate assets where applicable for client delivery can result in program/project delays and duplicative systems.
The primary strategic concerns in choosing an EA framework are:
- Stakeholders – CEO, COO and CIO are the strategic stakeholders and the executive sponsors of the EAPMO.
- Domain – Strategically, FedCon is interested in the alignment of business and IT operations and efficient processes.
FedCon has never stood up an EA practice and thus it would be wise to select an EA framework that could guide them in what to do and that it has been proven in the industry to be useful for organizations that are just starting out their EA journey. These high-level strategic criterions are fulfilled by The Open Group Architecture Framework (TOGAF) that provides an Architecture Development Methodology (ADM) as a step-by-step guide and includes how to do stakeholder management.
Politics at FedCon:
Generally, when we talk about politics in an organization we are referring to the negative connotations attached to it. But for our purposes, we will define politics to mean the formal power or informal power of an individual or group within an organization. The power exhibited by these individuals and groups can turn into obstacles or support to bring about organization-wide changes. In this sense, here we refer to formal power as the reporting structures while informal power refers to the influence yielded based upon the size of the BU, revenue generated by BU, the headcount of BU and close relationships of BU leadership with the executives.
At FedCon, even though the BU SVPs have the same title, they don’t have the same power. Taking this into account and the emphasis by the US Federal Government Executive Branch to focus on healthcare issues, the largest and most profitable among the FedCon’s BUs in the healthcare BU. Due to this reason, healthcare BU SVP has more informal power among its peers. This means that if the healthcare BU can be convinced of the merits of the EA practice then we can come one step closer to a FedCon-wide EA practice.
The primary political concerns in choosing an EA framework are:
- Stakeholders – BU SVPs, PMO and program/project managers are the political stakeholders. The BU SVPs have the formal power to bring change within their respective BUs. The PMO is a well-established office and it has visibility into the various kinds of projects and has informal power by pushing down changes to the project level within different BUs. Lastly, the program/project managers within BUs are stakeholders as well since they have to indoctrinate their teams on how EA can be used as leverage when developing client technology products and services.
- Domain – Politically, agreement, collaboration, and coordination across BUs and the corporate team seems to be the area of focus to rapidly bring technology products and services.
Due to the “friendly” competition among BUs to become bigger and yield more influence in FedCon, politics has to be carefully considered. Sometimes BUs are not willing to share if there are possible overlaps with what they are developing and what is already available in a different BU or at the corporate level. Convincing BUs to work together could be hard and caution has to be taken in which players to involve in the development of the EA practice. Additionally, there has to be some sort of collaboration between the EAPMO and PMO for lessons learned and organizational improvements. These high-level political criterions are also fulfilled by TOGAF where it recommends how Architecture Governance and Architecture Boards should be set up.
Innovation at FedCon:
Broadly speaking, innovation in organizations is disruptive, incremental or a combination of both. Disruptive innovation as described by the world-renowned management theorist Clay M. Christensen’s institute is such that it “transforms an existing market or sector by introducing simplicity, convenience, accessibility, and affordability where complication and high costs are the status quo.” This disruption can come in the form of unique business models, products and/or services that can give rise to new industries and improve existing industries. On the other end of the innovation spectrum, incremental innovation is where small changes are made to existing business models, products and services to improve existing industries.
Being a US Federal Government contractor, innovation at FedCon is mostly incremental since it tries to improve upon its existing products and services that are provided to the civilian agencies. FedCon accomplishes incremental innovation by obtaining customer feedback and assessing the competitive landscape. However, since BUs only focus on their own expertise, there are fewer opportunities for collaboration across BUs, which means technology products and services, are being developed without leveraging what already exists in the organization.
The primary innovation concerns in choosing an EA framework are:
- Stakeholders – FedCon employees that work directly with customers are the stakeholders that need to be considered since the improvement of existing technology products and services are highly dependent upon customer feedback and conveying of the feedback to FedCon.
- Domain – In terms of innovation, FedCon is interested in creating technology products and services that meet customer expectations and exceed what the competition can offer.
EA is a disciplined approach to accomplishing enterprise objectives through alignment between business and IT. This disciplined approach can also be leveraged to make FedCon more competitive, which can result in bringing technology products and services quicker to the marketplace. This high-level innovation criterion also points towards using TOGAF since it is constantly being improved upon based on the feedback from technology vendors and solution providers.
The culture at FedCon:
The “father of modern management” Dr. Peter Drucker once said that “Culture eats strategy for breakfast.” Culture can affect the ability of any organization to adopt or resist changes to the organization. While culture is typically considered a fuzzy attribute of an organization but there are tangible things that we can observe to decipher corporate culture which includes (1) corporate values, (2) employee recognition and risk-taking, (3) salaries, commission and hourly rates, (4) location, (5) clothes and (6) domain expertise and product/service subcultures.
At FedCon, the culture is such that change is welcomed as long everyone who is affected by it understands its purpose and there is no disruption to normal business processes. This is a two-pronged issue for the selection of an EA framework since even if the value of EA is understood by senior leadership but it is not understood at the BU, program/project and individual levels then it becomes just another information collection exercise.
The primary cultural concerns in choosing an EA framework are:
- Stakeholders – FedCon has a process-driven and metrics-monitoring culture. This is one of the reasons that the Program Management Office (PMO) is an important part of FedCon since it provides a consistent process by which programs/projects can be evaluated. In order to incentivize employees to change their behavior for the organizational transformation, human resources and accounting/finance offices are also stakeholders in EA success.
- Domain – Culturally, FedCon is interested in creating an atmosphere that encourages employees to take risks and leverage the massive intellectual property it has developed over the years to stay competitive.
One of the reasons for the success of the PMO within FedCon is its process-driven culture. So for the selection of an EA framework, we have to consider what plays into strengths of FedCon. This high-level cultural criterion leads us to TOGAF that provides a methodological approach for EA within an organization. The EAPMO would make use of lessons learned from the PMO to create a successful EA practice.
Execution at FedCon:
Intention without execution is simply thoughts without results. An organization can have great intentions but if it does not operationalize those intentions then all the strategy discussions and documentation it did just an exercise in futility.
At FedCon, execution has two views. One view is the execution based on winning a government contract to deliver technology products and services. The second view is the execution of the corporate strategy that looks into entering new markets, mergers and acquisitions and creating superior technology products and services.
The primary execution concerns in choosing an EA framework are:
- Stakeholders – All employees of FedCon at every level are stakeholders in the successful execution of EA.
- Domain – In terms of execution, best practices have to be applied/created for all of FedCon and metrics developed that assess organizational performance.
STANDING UP AN EAPMO:
After assessing the business environment of FedCon to determine an appropriate EA framework, next we have to determine people, processes and technologies needed to standup the EAPMO. These needs are discussed below:
People:
In order to assess the skill sets needed to run the EAPMO, we have to look at the current skillsets available, skillsets that people need to be trained on and hiring people with the necessary skillsets at FedCon. The hard skills needed to join the EAPMO require the knowledge of the chosen EA framework (i.e., TOGAF) and the ability to find common themes to enhance collaboration. The soft skills needed to join the EAPMO require (1) being politically aware, (2) ability to create bridges/connections and (3) high emotional intelligence. Additionally, metrics will be created to evaluate EAPMO team members based on their hard and soft skills.
Processes:
The business processes followed by EAPMO would be determined by TOGAF best practices and what has worked within FedCon. At a high level, this would be the architecture governance process and at the lower level, this would the cross-functional team’s processes for being advocates and collectors of information across FedCon. The various processes would be tested in the first 6 months to work out any wrinkles and get a baseline understanding of what needs to be done.
Technologies:
Now that we have selected the FedCon’s EA framework to be TOGAF, we have to select a tool that supports this framework. This tool can be selected by looking at Gartner’s Magic Quadrant for Enterprise Architecture Tools.
CONCLUSION:
Due to FedCon’s expertise as a technology company and for all the reasons stated in the analysis section, TOGAF is the right EA framework since it provides a roadmap of what needs to be done. One thing to keep in mind is that a framework needs to be flexible enough so it can adapt to changing organizational needs rather than the organization becoming a slave to the framework.
References:
- Khan, Arsalan. “5 Factors for Business Transformation.” Arsalan Khan. WordPress.com, n.d. Web. https://arsalanakhan.wordpress.com/2013/07/16/5-factors-for-business-transformation/
- “Stakeholder Management.” ADM Guidelines and Techniques – Stakeholder Management. TOGAF, n.d. Web. http://pubs.opengroup.org/architecture/togaf9-doc/arch/chap24.html
- Schekkerman, Jaap. Enterprise Architecture Good Practices Guide: How to Manage the Enterprise Architecture Practice. Victoria, BC: Trafford Pub., 2008. Print.
- “Architecture Governance.” Architecture Governance. TOGAF, n.d. Web. http://pubs.opengroup.org/architecture/togaf8-doc/arch/chap26.html
- Christensen, Clay M. “Christensen Institute.” Christensen Institute Disruptive Innovation Comments. Christensen Institute, n.d. Web. http://www.christenseninstitute.org/key-concepts/disruptive-innovation-2/
- “The Business Executive’s Guide to IT Architecture.” The Open Group Architectural Framework (TOGAF) Executive Overview. TOGAF, n.d. Web. http://www.opengroup.org/public/arch/p1/oview/
- Caldbeck, Ryan. “Why Execution Is Everything In Business.” Forbes. Forbes Magazine, 16 Sept. 2014. Web. http://www.forbes.com/sites/ryancaldbeck/2014/09/16/why-execution-is-everything/
- “Organisational Culture Eats Strategy for Breakfast and Dinner.” ORGANISATIONAL CULTURE EATS STRATEGY FOR BREAKFAST, LUNCH AND DINNER. Meliorate, n.d. Web. http://www.torbenrick.eu/blog/culture/organisational-culture-eats-strategy-for-breakfast-lunch-and-dinner/
- Lapkin and Weiss. “Ten Criteria for Selecting an Enterprise Architecture Framework”. Gartner report G00163673. Gartner http://my.gartner.com/portal/server.pt?open=512&objID=260&mode=2&PageID=3460702&resId=838915&ref=QuickSearch&sthkw=G00163673
- Brand, Saul. “Magic Quadrant for Enterprise Architecture Tools.” Gartner report G00263193 http://my.gartner.com/portal/server.pt?open=512&objID=260&mode=2&PageID=3460702&resId=2859721&ref=QuickSearch&sthkw=ea+tools+magic+quadrant









You must be logged in to post a comment.