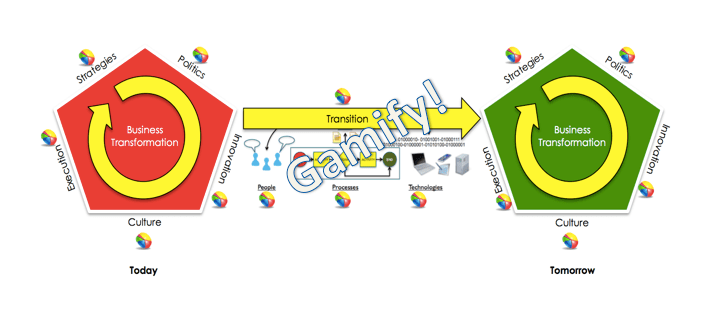
For some organizations, December/January is that time of the year where organizations reflect on what happened during the prior year and what goals need to be accomplished for the current year. This reflection revolves around the organization’s people, processes and technologies. It also involves creating strategies, understanding the effects of internal and external politics, competing innovatively, transforming culture and polishing execution. In order to thoroughly learn and objectively plan, the right questions need to be asked. These questions open the organization to have a better understanding of what has happened and helps in determining what needs to happen. By no means, these are the only questions to be asked but rather should be used as a starting point to go beyond a mere surface-level understanding of issues. So, let’s ask them:
|
Today |
Tomorrow |
| Who develops the strategy? | Who should develop the strategy? |
| What internal and external politics affected your organization? | What internal and external politics should not affect your organization? |
| Where did the inspiration for innovation came from? | Where inspiration of innovation should come from? |
| When culture trumped strategy? | When should culture trump strategy? |
| Why execution was flawed? | Why execution would continue to be flawed in the future? |
When you are asking the above questions, keep in mind that organizational silos have to be broken down to create a well-oiled machine where all gears interconnect with each other and understand each other’s roles and responsibilities. An organization that can consistently set goals, track them and measure them against expectations, have better data to make informed decisions.
In conclusion, take this time to understand the multidimensionality of your organization. New Years is about reboot; reboot your organization to become a disruptive force; reboot so that your employees, partners, customers, and stakeholders become your megaphone; reboot your business processes to bring products and services quickly to the market; reboot to create a learning organization; reboot to make data open your eyes to new possibilities and reboot to create an organization that positively serves people beyond perceived organizational boundaries.






You must be logged in to post a comment.