In his article, Nick Carr argues that in the current business environment Information Technology (IT) does not provide any strategic advantage but it is merely an operational necessity. He equates IT to a commodity much like electricity and mainly talks about IT infrastructure becoming a commodity. Let’s explore this in the context of the Internet and Internet technologies:
The Internet:
The Internet is a network of networks that connects varied computers via switches to allow transmission of data across multiple networks using Internet protocols. Some of the popular uses of the Internet include email, instant messaging, browsing the World Wide Web (WWW) to name a few. In today’s society, the Internet has become an important tool for individuals and organizations to conduct their business. It seems like the use of the Internet has become so ubiquitous that individuals and organizations don’t even think about it and assume it to be always available but does that mean the Internet has become a commodity. In this context, I would agree with Nick that the Internet has now become very similar to a commodity since we are all accessing the same Internet despite the mediums by which we access it.
Internet Technologies:
Internet technologies include browsers and search engines that help us navigate the WWW of the Internet. From Nick Carr’s perspective, these Internet Technologies are commodities and do not provide any strategic value. I disagree with this claim and here is why:
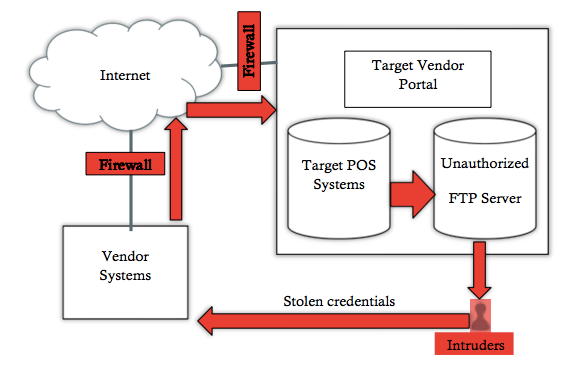
- Browsers: Currently browsers are used to browse the WWW and used internally by organizations to access their corporate systems such as Enterprise Resource Planning (ERP) and Customer Relation Management (CRM) systems via a web interface. Thus, the security and privacy capabilities of these browsers become paramount in safeguarding the organizations against malicious attacks. While from the surface it may seem that these browser issues are operational in nature but from a closer inspection we can understand their strategic importance. For example, if an organization chooses one browser over another browser that has less security then the organization becomes vulnerable to exploits of that browser. These exploits can entail simple hacking attacks on the siphoning of organizational data. So, the selection of a browser is not just an operational activity but I believe it to be a strategic necessity.
- Search: A McKinsey report, The Impact of Internet technologies: Search, indicated that web search provides value that includes the creation of new business models. An example of this would be price comparisons where users can essentially compare prices of what they are buying (e.g., airline tickets, hotel rooms, etc.) from various vendors on one website. This price comparison is not only useful for users but for corporations, this could also be used to determine if they are competitively priced. Since making your organization competitive is also a strategic consideration thus search capabilities are important for the organization’s future.
In conclusion, the oversimplification and lack of understanding of how the nuances of technology can affect organizations strategically are not only unsettling but also ill-informed. IT is not just one thing and by saying it is and cherry-picking the data to show this can lead to unintentional consequences.
References:





You must be logged in to post a comment.